Startups
Crayonic

Crayonic develops hardware module to secure digital identity for people and things. We refer to itas Crayonic Identity Core or CIC . CIC hardware module is running Crayonic Identity firmware which will soon be open sourced. These two technologies combined are the basis for all identity projects with in our company and soon it will be available to anyone wishing to develop projects where secure identity plays a major role. This technology is protecting identities in all types of digital interactions: person-to-person(P2P) , person-to-machine (P2M), machine-to-machine (M2M).
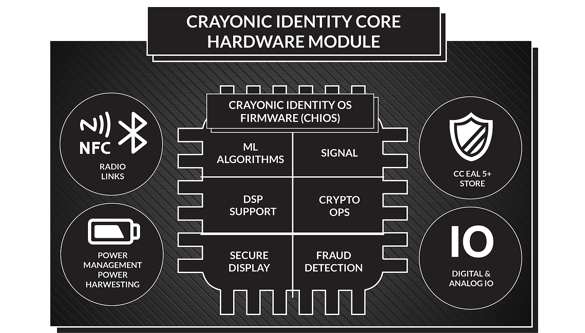
Our hyper-secure, yet human-friendly, technologies use all three security factors - knowledge, ownership and inherence, while IOT devices developed by Crayonic protect data in the field with the same security as offered by blockchain. In fact, IOT devices using Crayonic technology can directly interact with blockchainsas their secure front-end.