Apply
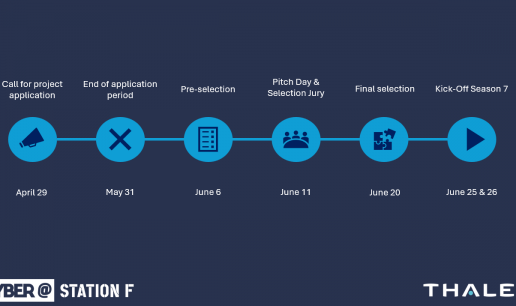
Join us at Station F!
Each acceleration is based on technological challenges in order to meet Thales and its customers' stakes in cybersecurity with the right startups. Find out here the challenges for the season 7, starting in June 2024.


CHALLENGES
In order to target the type of solutions we are looking for, we have set up a list of challenges that you can find below.


JOIN THE ADVENTURE
If you are interested in our program, you can apply by clicking on the link below.